At CIX-A we believe in sharing our knowledge between members but also from time to time with the whole cyber ecosystem.
Here is a small example about enriching and qualifying OSINT when not totally complete. Of course we benefit of our CTI platform to share enriched information with our member, they can search in or pull to their systems with our API.
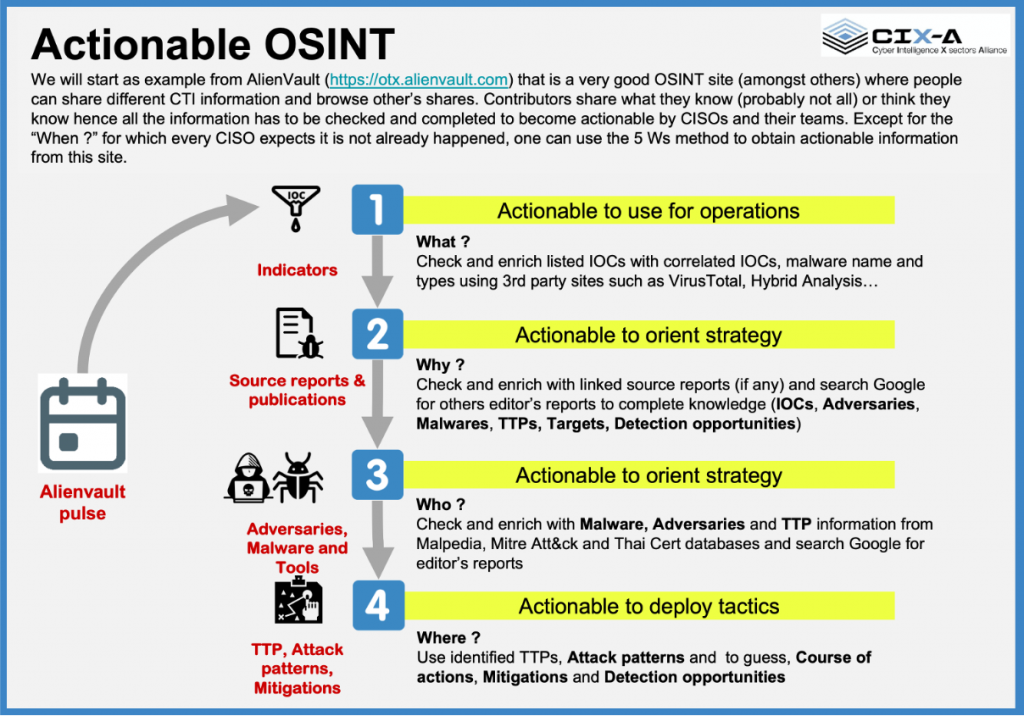
This is in very short words how members contribute, including many other OSINT sources, checks and reports automatically fed and manually enriched in our CTI ThreatQuotient platform.
Each enrichment benefits all members who have access to that platform or its API to benefit of crosschecked, qualified and complete information to orient strategy, deploy tactics and use appropriate informations for their operations.
We are happy to receive your suggestions and comments on our contact email or via our LinkedIn and Twitter accounts
Glossary :
AlienVault Pulse : Each information upload in the Open Threat eXchange OSINT platform is named a pulse. Our CTI platform automatically pulls selected pulses and integrate the corresponding information in database.
Indicator : Actionable information about a threat. That information may be an IP address, a hash of a file, an URL or a domain name. Indicator can be associated with a malware, an APT group which give information to the CISOs and their teams.
TTP: Behaviors of a threat actor : technics, tactics and procedures used by the actors to hack systems, maintain presence, set remote access and communications. TTP informations is mostly implemented in our CTI platform using Mitre Att&ck framework Attack Patterns and Mitigations.